Data Loss Prevention Solutions
Important of Data Loss Prevention
Data Loss Prevention (DLP) refers to a set of strategies, technologies, and practices designed to prevent unauthorized access, use, or leakage of sensitive information. DLP solutions monitor and control data transfers across your network, ensuring that confidential information is protected from loss or theft.
DLP is crucial because it helps safeguard sensitive data from accidental or malicious breaches, reducing the risk of financial loss, reputational damage, and legal consequences. By implementing DLP measures, organisations can ensure compliance with data protection regulations, maintain customer trust, and secure valuable intellectual property, all while mitigating the risk of data-related incidents.
What Does White Rook Cyber Offer?
At White Rook Cyber, we provide cutting-edge Data Loss Prevention (DLP) solutions to ensure your organisation’s critical information remains secure and intact.
Our expert team implements comprehensive DLP strategies tailored to your needs, focusing on preventing unauthorised access and mitigating risks of data breaches.
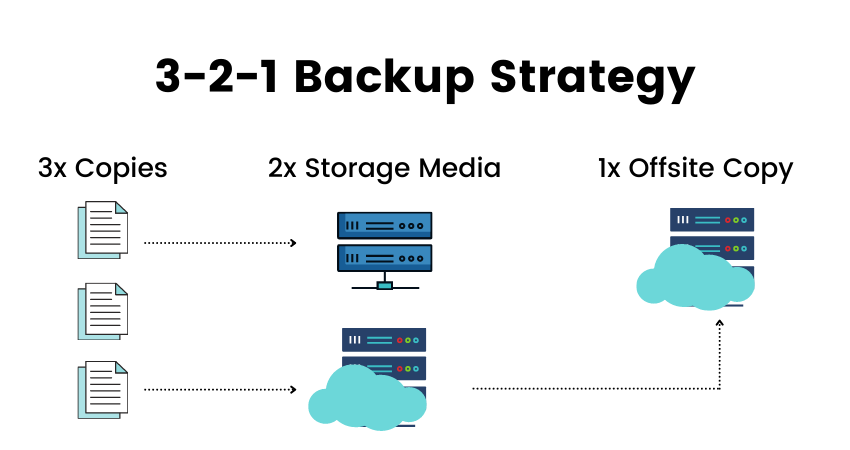
We integrate the proven 3-2-1 backup principle into our approach, ensuring that you have three total copies of your data, two of which are stored locally but on different devices, and one copy stored offsite. This multi-layered backup strategy enhances your resilience against data loss from various threats, including cyberattacks, hardware failures, and accidental deletions.
With White Rook Cyber’s DLP solutions, you benefit from robust data protection, compliance with industry standards, and peace of mind knowing your vital information is securely backed up and safeguarded against potential threats.
Implements advanced DLP strategies to safeguard your sensitive information from unauthorized access, breaches, and loss.
Utilizes the 3-2-1 backup strategy to ensure robust data resilience, with three total copies of data, two stored locally, and one offsite for maximum security.
Tailors DLP measures to fit your organisation’s specific needs and risks, providing effective protection against various data loss scenarios.
Helps you adhere to data protection regulations and industry standards, enhancing your organisation's security posture and maintaining customer trust.
Holistic Protection. Hassle-Free. Cost-Effective.
Let us help you take your Cyber Security to the next level!
Our Managed Cyber Security Service Includes:
Why Choose Us?
In today’s digital landscape, robust cyber security is not just a necessity but a strategic advantage. At White Rook Cyber, we offer a comprehensive suite of services designed to protect, detect, and respond to threats with precision and agility.
Our 24/7 Security Operations Center (SOC) and SIEM services ensure real-time threat detection and response, leveraging advanced technologies and seasoned experts to keep your systems secure.
Our Governance, Risk, and Compliance (GRC) audits help you navigate complex regulatory environments and strengthen your security posture with actionable insights and tailored strategies.
With our Penetration Testing, Red Team, and Purple Team engagements, we simulate sophisticated attacks to identify and address vulnerabilities before malicious actors can exploit them.
We understand that every organisation is unique. Our solutions are tailored to meet your specific needs, ensuring maximum protection and compliance while minimizing disruption to your business operations.

Testimonials
Viktor Vukovic
“Partnering with White Rook Cyber we can proactively plan and undertake necessary cyber security assessment and testing activities to safeguard sensitive information and organisational integrity. This partnership has helped us to develop an appropriate roadmap for our business that enables us to understand our current state against an industry recognised cyber security framework. While assisting us to prioritise targeted strategies effectively to achieve our desired level of security maturity”
We Are Here to Help!
Secure your digital world with our expert cyber security solutions. Contact us today to protect your business from online threats.
Send Us Message
Let us know how we can help!









